- Forbes seamlessly consolidated organization to Google Drive for user collaboration and storage in only 10 days.
Growing at 50%+ a year, the explosion of emails, documents, images, PDFs, etc. are potential vulnerability points for brand impact, corporate liability and fines. As these rising depots of unstructured data continue to grow, legacy and often siloed approaches have offered little insight into the risks — obscuring sensitivity, security, ownership, sharing rights and other potential risks.
Make better, informed decisions faster — with data driven intelligence
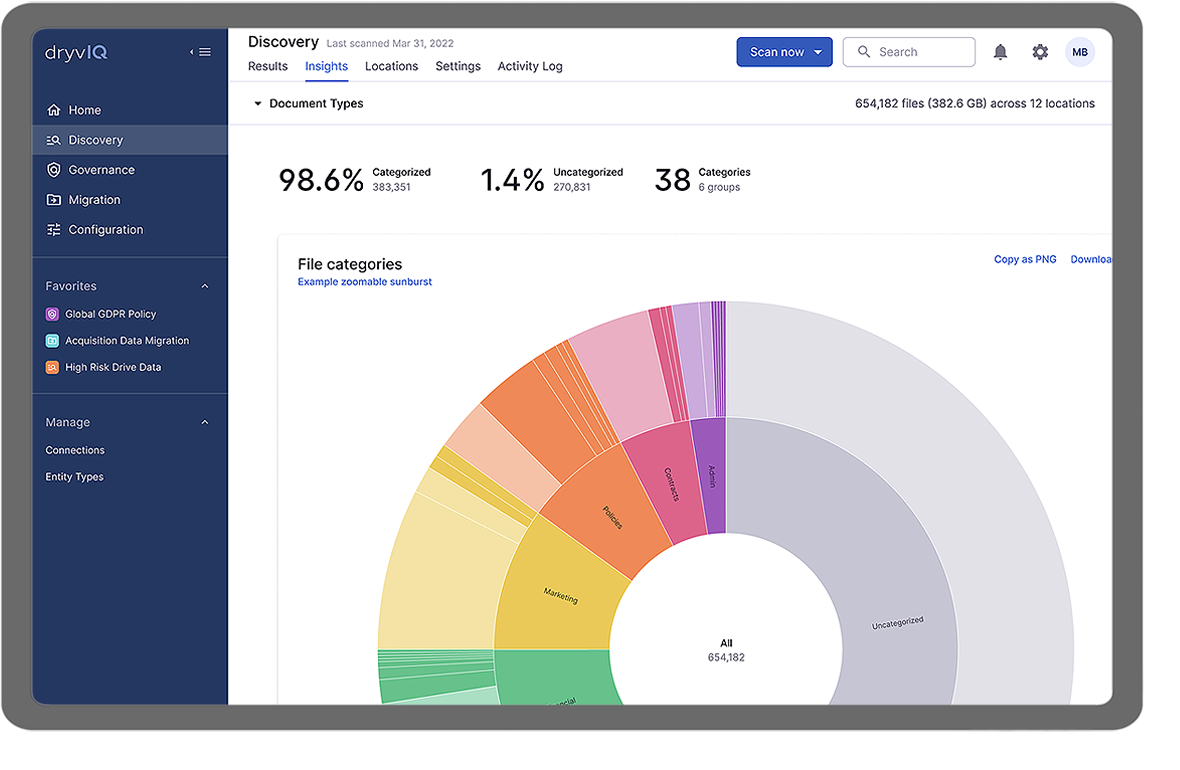
Driven by advanced artificial intelligence, DryvIQ continually detects, analyzes, and classifies sensitive and other valuable data and labels the degree of criticality — at scale. It discovers a wide array of aspects of your unstructured data including sensitivity levels, age, type, last-accessed, location, permissions access and both internal and external sharing rights and more.
Improve security posture and compliance
While DryvIQ detects, classifies, and labels sensitive information as part of the sensitivity label application — governance capabilities ensure that data is properly authorized and stored in the appropriate location. The platform is able to add additional permissions and/or move files to a secured folder, system or geo-location to meet content residency compliance
Policy-driven classification can be leveraged to automate the application of sensitivity labels to enrich Data Loss prevention (DLP) and other Digital Rights Management (DRM) systems to ensure that intellectual property is not leaked outside the organization.
"DryvIQ was incredibly responsive and truly delivered on their promise."

We were shocked and happy that we were able to complete project on deadline.
Increase corporate agility without limiting user productivity
DryvIQ leverages the latest technology to help protect your data and reputation while future proofing your investments. A strong data governance strategy is a difficult balance between properly protecting data while providing the appropriate rights and permissions to the end user to do their job efficiently. It enforces your data governance strategy, empowers end users and provides continuous oversight to ensure that all data is properly protected.

