Schedule a demo to see DryvIQ’s intelligent data classification in action, or speak with one of our experts today.
Classify your data. Enact proper controls. Drive business value.
Business never stops, and neither does the growth of your unstructured data. Today, it makes up the vast majority of enterprise content, carrying hidden risks and untapped potential.
DryvIQ’s advanced data classification capabilities make it easy to discover, classify, and manage unstructured data continuously, in-place, and at scale. Our intelligent data classification capabilities help you:
- Fuel AI Initiatives: Prepare high-quality, curated data sets for machine learning, copilots, agents, and AI applications.
- Reduce Risk: Identify and protect sensitive information like PII, PHI, user credentials, financial data, IP, and more.
- Ensure Compliance: Ensure adherence to evolving regulations like GDPR, HIPAA, GLBA, PCI-DSS, and CCPA.
- Drive Efficiency: Streamline data management by eliminating redundant, obsolete, and, non-critical data.
Whether you’re preparing data for AI initiatives, tightening security, or simplifying regulatory audits, DryvIQ ensures your unstructured data is always organized, business-ready, and under control.
Unlock the full value of your unstructured data by making it relevant, organized, clean, and secure
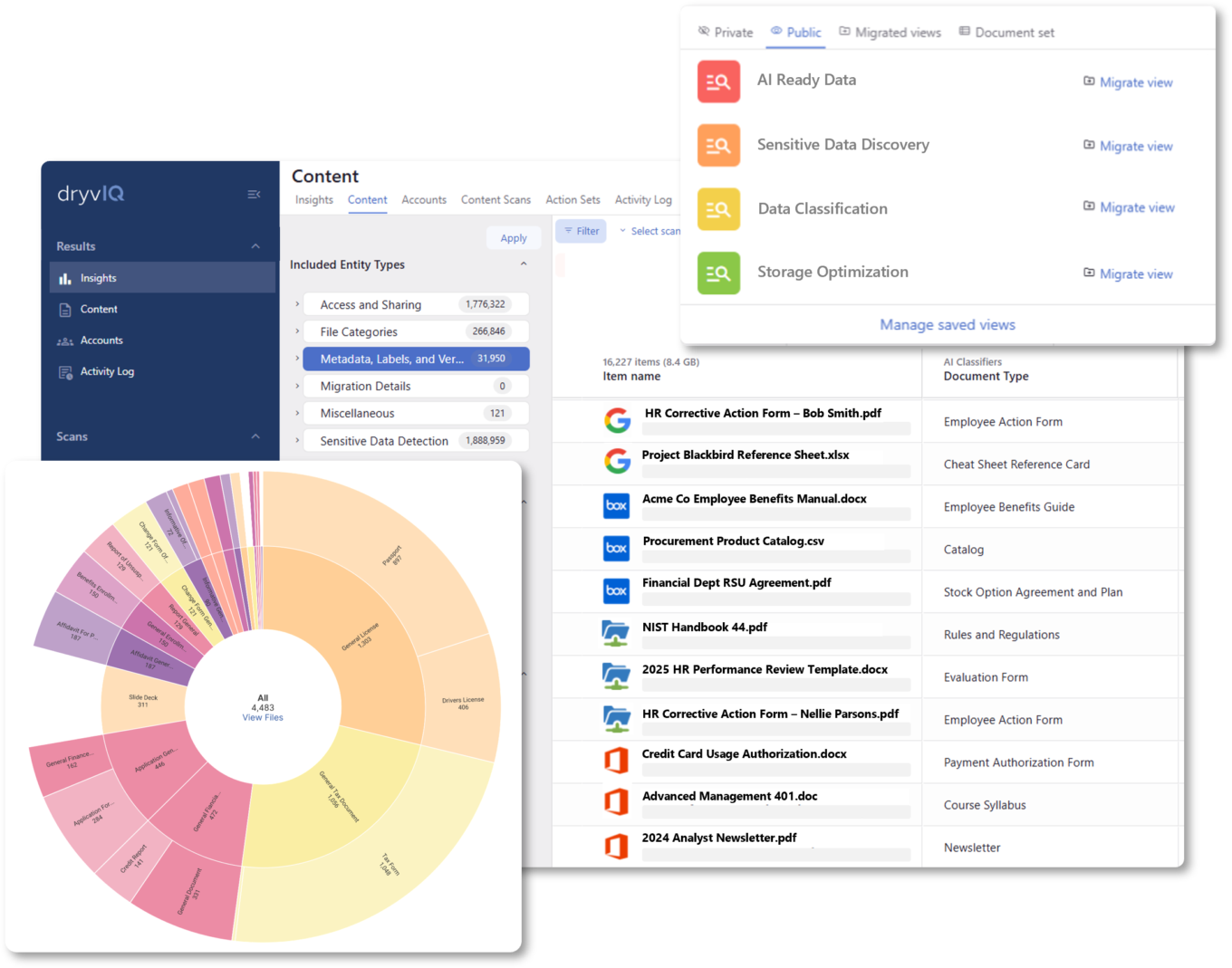
DryvIQ’s patented AI-driven discovery and classification engine continuously scans, analyzes, and applies classification labels across 40+ content repositories —on-premises and in the cloud. The DryvIQ platform identifies file content, context, sensitivity, and usage to assign meaningful classifications that align with your business rules and compliance frameworks.
Key Capabilities:
- Visualization of classified data across your content landscape
- Automated discovery and classification of sensitive data (PII, IP, PHI, etc.)
- Dynamically categorize by department, owner, document types, sensitivity or business use
- Classify data with insights from age, last-accessed, obsolescence, and duplication
- Advanced rule-driven tagging and labeling, including MPIP labels and Box Shield labels based on metadata and file content
- Integration with Microsoft Purview, Box Governance and other governance tools with increased control and flexibility
Nicolet National Bank strengthens its security posture with data classification
DryvIQ was able to scan and identify Nicolet National Bank’s IT data, assess its sensitivity, and classify it accordingly – delivering accuracy rates up to 92 percent. In addition to a stronger security posture, Nicolet now has the intelligence to make decisions that can increase efficiencies in data management.

Between the speed and accuracy of the platform and working with the DryvIQ team, it’s just been incredible.
